Crack that Code!  Jefferson's disk cipher Jefferson's disk cipher This week in class we continued the theme of looking for patterns in numbers. Students were introduced to several methods for encrypting and decoding messages using ciphers. We looked at Frequency Analysis - the process by which the frequency of a letter in an encoded message is compared with the frequency of letters in English words. The letters that occur most frequently in the ciphertext will likely correspond to the letters that occur most frequently in English words. Students worked together in class using this method to decode a message from William Shakespeare’s play Julius Caesar.  Next, we looked at a method of encryption where each letter is replaced with a letter a specified distance ahead in the alphabet. Such a system is known as a Caesar cipher because Julius Caesar is thought to have used this method to communicate with officers in the Roman army. When sending a message, Caesar would inform his generals what the shift was, so they would be the only ones who could read the encrypted message. Students created their own Caesar Cipher Wheels and worked on encrypting and decoding messages. We agreed that "substitution ciphers" like the Caesar cipher which have a one-to-one correspondence can be fairly easy to crack. But what if we created a cipher with a one-to-many letter correspondence? These "polyalphabetic ciphers" pose more decoding difficulty than a simple substitution cipher. Instead of one shifted alphabet being used, multiple shifted alphabets are used, based on a keyword. One such example is the Vigenere cipher shown HERE. For homework this week, I provided students with the fun and challenging problem of "The Dancing Code Men". These codes are taken from the Sherlock Holmes’ mystery The Adventure of the Dancing Men by Sir Arthur Conan Doyle. Students should use their decoding skills to crack the code and reveal all six encrypted messages. For those interested in reading the entire story, you may find it HERE (though, it's not necessary to solve the problem). Have fun! (: The cipher lesson was created using resources from NCTM Illuminations.
Comments are closed.
|
Categories
All
Archives
May 2016
|

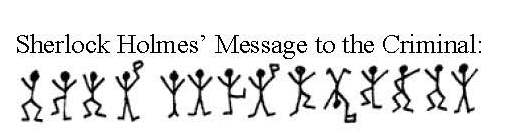
 RSS Feed
RSS Feed